Virtual Home Lab Setup for Cybersecurity - Part 10: Configure Attacker Machines
Part 10 - Configure Attacker Machines
Overview
In this part, we’ll configure three attacker machines: Kali, Parrot and BlackArch. If you haven’t already, download Kali from here, Parrot from here and BlackArch from here.
Kali Installation and Configuration
This one is easy, follow through the steps in Part 2 exactly as they are, making only one change:
In the “Network” setting of the VM, make sure the “Attached to” is “Internal Network” and the “Name” is “LAN 5”. The “Adapter Type” should be paravirtualized network.
Once the VM is setup, run the update and upgrades commands, take a clean snapshot and it is good to go!
Parrot Installation and Configuration
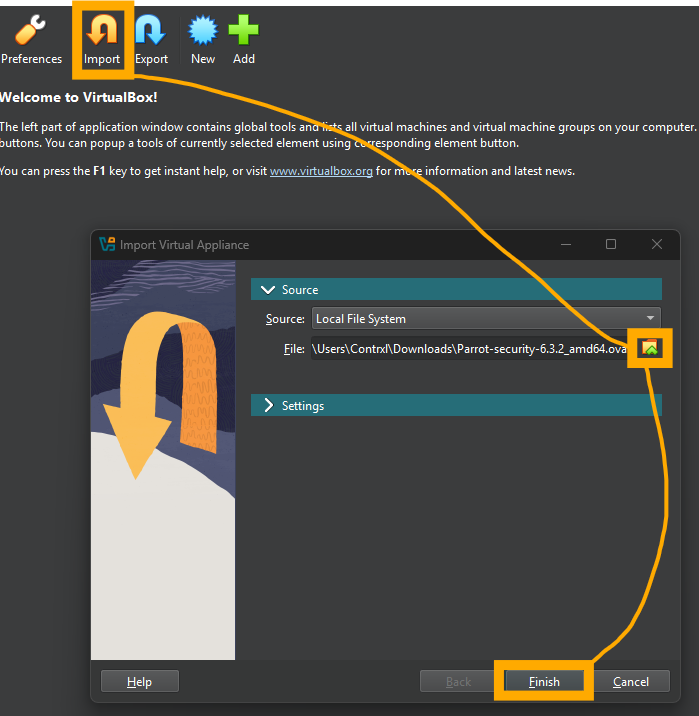
To install the Parrot OS .ova file we downloaded, select “Import” from the VirtualBox tools menu. Selec the small folder icon to open your file explorer, then navigate to where you downloaded the .ova file, select it and then “Finish”.
Agree to the license terms popup and wait for the import to complete. Once imported, click the VM and open settings. Under “System” then “Motherboard” the default “Base Memory” is 8GB. You can turn this down to 4GB if it is too intensive. Under “Network”, change “Attached to” to “Internal Network” and the “Name” to “LAN 5”. The “Adapter Type” should be “Paravirtualized Network”. Press “OK” to finalise and boot the VM. Once the machine is booted, run sudo apt update && sudo apt upgrade from terminal to update. Power down the VM and take a snapshot of the clean installation.
BlackArch Installation and Configuration
To install the BlackArch .ova file, follow the same procedure we did for Parrot. Choose “Import” and select the downloaded file. Wait for the import to complete. Once imported, select the VM then “Settings”. Select “Network” and change adapter one to “LAN 5” like the other two machines. You can boot it to make sure all looks ok, then power it off and take a snapshot.
Arch is a little intense, so consider this an optional addition, its not super necessary/mandatory for anything that I typically do.
That’s all for the attacker range! Next, we’ll configure the vulnerable CYBER range to actually attack.